Ethical Hacking Practices in Cybersecurity

As cyberthreats grow in complexity and frequency, the need for robust security measures is more critical than ever. Ethical hacking proactively identifies and addresses vulnerabilities before malicious actors can exploit them. By simulating potential attacks, ethical hackers help organizations strengthen their cybersecurity frameworks, protect sensitive data, and ensure the continuity of their operations. Let’s explore ethical hacking and see what you must do to enter this rewarding and crucial job field.
What Is Ethical Hacking?
Ethical, or white-hat, hackers use the same techniques as malicious hackers to uncover and fix security vulnerabilities in networks or computer systems. White hats mimic how cybercriminals would break into a network and show what damage they could potentially do. Ethical hacking aims to help an organization improve its security systems.
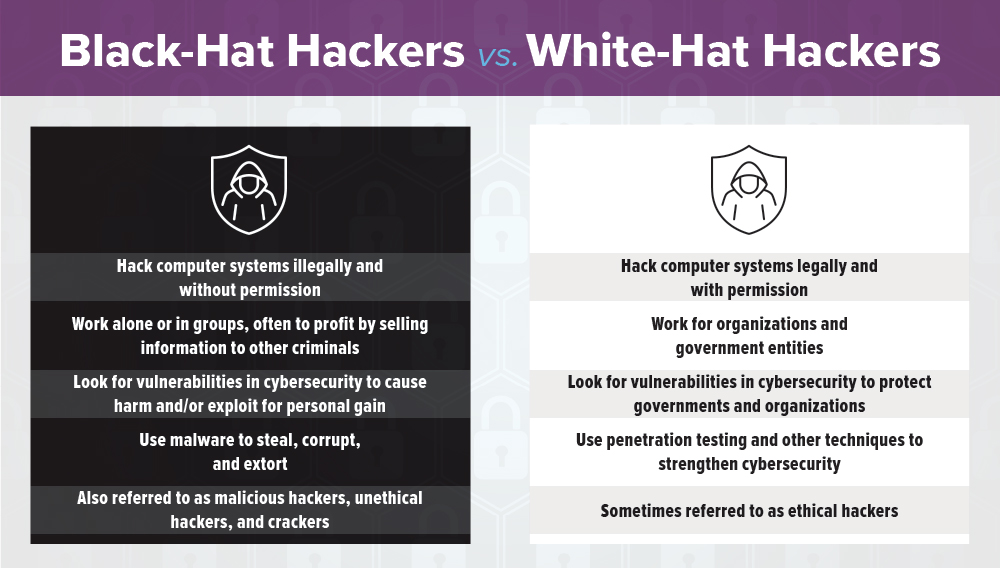
What Is the Difference Between Black-Hat and White-Hat Hackers?
The main difference between black hats and white hats is that white-hat hackers use their skills for ethical purposes, whereas black hat hackers engage in illegal activities for criminal reasons. There are also many other types of hackers who play various roles, but the main hackers to know are white hats and black hats. Let’s explore some of their main differences:
Black-Hat Hackers
- Hack computer systems illegally and without permission
- Work alone or in groups, often to profit by selling information to other criminals
- Look for vulnerabilities in cybersecurity to cause harm and/or exploit for personal gain
- Use malware to steal, corrupt, and extort
- Also referred to as malicious hackers, unethical hackers, and crackers
White-Hat Hackers
- Hack computer systems legally and with permission
- Work for organizations and government entities
- Look for vulnerabilities in cybersecurity to protect governments and organizations
- Use penetration testing and other techniques to strengthen cybersecurity
- Sometimes referred to as ethical hackers; in teams, can be referred to as sneakers, hacker clubs, red teams, or tiger teams
What Is Penetration Testing?
One of the techniques white-hat hackers use to help organizations discover their network’s vulnerabilities is penetration testing, or pen testing for short. Penetration testers simulate cyberattacks to identify vulnerabilities that malicious hackers could exploit. This testing may include social engineering, phishing, and exploiting weak passwords. It can be conducted using approaches like black-box testing and white-box and gray-box testing. Pen testing helps organizations identify and fix security weaknesses, meet regulatory compliance, protect reputations, and improve security. Cybersecurity experts recommend penetration testing and support regulatory compliance.
How Can I Prepare for a Career in Ethical Hacking?
If you think a career in ethical hacking is in your future, the first step is pursuing the right education. An associate or bachelor’s degree in information technology, cybersecurity, or computer science is a good way to help you apply for entry-level positions, and a master’s degree can help you advance in cybersecurity. It’s also important to gain experience working as an ethical hacker in entry-level positions or internships.
Earning ethical-hacking certification can also help you become proficient in hacking techniques. Some popular industry certifications include Certified Information Security Professional (CISP), Certified Ethical Hacker (CEH), CompTIA Security+, CompTIA Network+, Computer Hacking Forensic Investigator (CHFI), and Systems Security Certified Practitioner (SSCP).
Ethical hacking is an essential and dynamic field, offering vital services to protect organizations from ever-evolving cybercrime. As cyberthreats grow, the role of ethical hackers becomes increasingly crucial. With opportunities spanning various industries and the chance to work on the cutting edge of technology, a career in ethical hacking provides the satisfaction of contributing to a safer digital world.



